|
T. Andrew Yang Email: yang@uhcl.edu Web: http://cse.uhcl.edu/yang/ Tel.: (281) 283-3835 |
Last updated: 3/30: revised class
schedule in response to changes caused by the virus 2/19:
updated due dates for research draft (4/8) and lab 3 (4/15) 2/11:
Lab 1 published; updated due dates 2/5:
updated due dates (3/4, 4/15, 4/30) for the research project 2/5:
updated hands-on labs information 1/29: TA hours revised 1/26:
TA hours posted 1/22:
fixed Assignment 1 link, and updated TA hours 1/22:
first posted |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Time
& Classroom Wedn., 1:00pm – 3:50pm (Delta 201) Prerequisite: Web
Applications Development (csci/cinf4230)
and Computer Security (csci/cinf4233 or
csci5233), or instructor's approval. Note: If you do not have either
of the prerequisites, you MUST talk to the instructor. It is assumed that
students enrolled in this class are familiar with fundamental topics such as
cryptography (symmetric vs asymmetric encryptions/decryptions), security
protocols (RSA, DES, Triple-DES, digital signatures, digital certificates,
etc.), and n-tier web applications development. Course Description: Fundamental
coverage of issues and techniques in developing secure web-based
applications; related topics such as network security, web server security,
application-level security and web database security, etc. Course Objectives: The
primary objective of this course is to study and practice fundamental
techniques in developing secure web-based applications, including
vulnerability of web-based applications and how to protect those applications
from attacks. In addition, advanced topics related to Web, such as E-commerce
security, Cloud security, collaborative Web-based applications, etc., will
also be studied. Students are encouraged to complete a publishable research
paper on one of the related topics. Learning Outcome:
·
Understand
security-related issues in Web-based systems and applications. ·
Understand the
fundamental security components of a computer system. ·
Be able to evaluate a
Web-based system with respect to its security requirements. ·
Understand the process of
developing secure networked systems. ·
Understand the
fundamental mechanisms of securing a Web-based system. ·
Be able to implement
security mechanisms to secure a Web-based application. ·
Understand security
issues and common controls in electronic commerce systems. Class Format: Lectures
are combined with discussions and, if applicable, student presentations and
discussions of advanced topics. Students are expected to be active
participants, by studying the relevant chapters and/or research papers, and
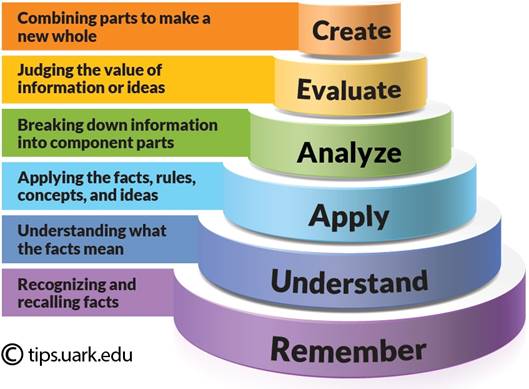
participating at in-class discussions. A note about Bloom's Taxonomy
and your learning …
(source: https://tips.uark.edu/using-blooms-taxonomy/
) Instructor:
Dr. T. Andrew Yang
Teaching assistant info and office hours: TA
- Bikkumalla,
Darshitha (BikkumallaD6604@UHCL.edu)
Office Hours – Monday 4
pm - 8 pm Note: Contact the instructor immediately if you have got any problem with the TA or the office hours. Required Text:
+ Instructor's handouts in the class and/or on the Web Supplemental
Materials
o
Architecture
of Oracle Net Services o
Oracle's Listener
Control Utility (lsnrctl) o
Transparent
Network Substrate (TNS)
o SSL Configuration HOW-TO, the Apache Tomcat 5.5 Servlet/JSP Container:
http://tomcat.apache.org/tomcat-5.5-doc/ssl-howto.html
Glossaries, RFCs, Related Websites, etc.
o
RFC2828: Internet
Security Glossary. R. Shirey. May 2000. o
http://www.netlingo.com: searchable
online dictionary o
http://www.sharpened.net/glossary/index.php:
Definitions of Computer and Internet
Terms
o
o
o
o
o
o
o Searching the RFC database: https://www.rfc-editor.org/ o The Internet Engineering Task Force (IETF): http://www.ietf.org/ o RFC2616:
Hypertext Transfer Protocol -- HTTP/1.1. R. Fielding, J. Gettys, J.
Mogul, H. Frystyk, L. Masinter,
P. Leach, T. Berners-Lee June. June 1999. DRAFT STANDARD. local copy of rfc2616 o RFC2617:
HTTP Authentication: Basic and Digest Access Authentication. J. Franks,
P. Hallam-Baker, J. Hostetler, S. Lawrence, P. Leach, A. Luotonen,
L. Stewart. June 1999. DRAFT STANDARD. local copy of
rfc2617 o RFC2965:
HTTP State Management Mechanism. D. Kristol, L. Montulli.
October 2000. PROPOSED STANDARD. local copy of rfc2965
o RFC2585:
Internet X.509 Public Key Infrastructure Operational Protocols: FTP and HTTP.
R. Housley, P. Hoffman. May 1999. PROPOSED STANDARD. local copy of rfc2585 “This document specifies the conventions for using the File Transfer
Protocol (FTP) and the Hypertext Transfer Protocol (HTTP) to obtain
certificates and CRLs from PKI repositories.
Additional mechanisms addressing PKI repository access are specified
in separate documents.”
o RFC2246:
The TLS Protocol Version 1.0. T. Dierks, C. Allen. January 1999. PROPOSED
STANDARD. local copy of rfc2246 o RFC2712:
Addition of Kerberos Cipher Suites to Transport Layer Security (TLS). A. Medvinsky, M. Hur. October
1999. PROPOSED STANDARD. local copy of rfc2712 o RFC2817:
Upgrading to TLS within HTTP/1.1. R. Khare, S.
Lawrence. May 2000. PROPOSED STANDARD (Updates RFC2616). local
copy of rfc2817 o RFC2818:
HTTP over TLS. E. Rescorla. May 2000. INFORMATIONAL. local
copy of rfc2818 o RFC2830:
Lightweight Directory Access Protocol (v3): Extension for Transport Layer
Security. J. Hodges, R. Morgan, M. Wahl. May 2000. PROPOSED STANDARD
(Updated by RFC3377). local copy of rfc2830 o RFC3268:
Advanced Encryption Standard (AES) Ciphersuites for
Transport Layer Security (TLS). P. Chown. June
2002. PROPOSED STANDARD. local copy
o
RFC2827/BCP0038:
Network Ingress Filtering: Defeating Denial of Service Attacks which employ
IP Source Address Spoofing. P. Ferguson, D. Senie.
May 2000. BEST CURRENT PRACTICE. local copy o
RFC3377:
Lightweight Directory Access Protocol (v3): Technical Specification. J.
Hodges, R. Morgan. September 2002. PROPOSED STANDARD. local
copy of rfc3377
o
Man in the middle
attack as explained on Wikipedia o
Bejtlick, Richard. "Implementing
Network Security Monitoring with Open Source Tools": Interesting
discussions of net monitoring issues, including open source tools such as tcpdump, argus, snort,
trafd/trafshow, sguil, etc. o
VeriSign Technical
Brief. "Building an E-Commerce
Trust Infrastructure: SSL Server Certificates
and Online Payment Services" o
Cryptography FAQ Index: http://www.faqs.org/faqs/cryptography-faq/
o
Cryptography.org: http://www.cryptography.org/ o The Open SSL Project (SDKs for free download): http://www.openssl.org/ ·
SEEDS Security labs: https://seedsecuritylabs.org/ ·
SEEDS Web Security labs:
http://www.cis.syr.edu/~wedu/seed/labs12_04.html ·
Computer & Internet
Security - Slides, Problems and
Labs: https://www.handsonsecurity.net/resources.html Topics and Notes
++ Attendance Policy: You are
expected to attend all classes. There will be no penalty for a person’s first two absences without documented excuse. 1% will be
taken for each of the absences after the first two absences without excuse.
Note: Being tardy is no excuse
when a person is found to be absent from the class. Note: If you ever miss a class, it is your responsibility to get
hold of whatever may have been discussed in the class. +++ Class Participation:
Participating in the class is
expected. You should ask or answer questions during the in-class or online
discussions. Grading Scale: The
accumulated points from all the categories determine a person's final grade. There
will be no extra-credit projects.
Exemption from the final exam: Students who have performed fantastically before the
final exam may be exempted from taking the final exam.
Tests & Exams: Both
analytic and synthetic abilities are emphasized. Being able to apply the
learned knowledge toward problem solving is also highly emphasized in the
tests. Unless
due to unexpected, documented emergency, no make-up exams will be given. No make-up exams will be granted once the exams have been
corrected and returned to the class. Assignments
and projects will be posted at the class web site. Assignments &
projects are due before the beginning of the class on the due day. See Topics and Notes for the due dates. a. Identification page: All assignments must have your
name, and course name/number/section number (e.g., CSCI5234-01) at the top of
the first page. b. Proper stapling: Staple all the pages together at
the top-left corner. NOTE: Do not use paper clips. c. Order ! Order! Arrange the solutions following the
sequence of the questions. Write the question number at the top-right corner
of each page. d. Word processing: It is required that you type your
reports (e.g., print them using a printer). Use a word processor and
appropriate typesetting and drawing tools to do the assignments. Spell-check
the whole document before printing it. You may lose points due to spelling or
grammatical errors. Projects: The
projects will involve the design and implementation of encryption/decryption
algorithms and/or application of the algorithms to real-world problems.
Students are expected to employ the theories and techniques learned in the
class to design the system. Details
of the projects will be later made available at Assignments
& Projects. NOTE:
Unless otherwise
specified, all assignments and projects are individual work. Students should take caution not to
violate the academic
honesty policies. Check out the details at this
link. Instructor's Notes:
Go to the Index |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||